

The threat of cyber-attacks is growing with each passing year and does not only affect large enterprises or critical infrastructure. In addition to an increase in malware variants, which play a particularly large role in the encryption of data and the associated extortion, increasingly sophisticated attacks are also being carried out by state-organized hacker groups (APT). The attacks on SolarWinds and Microsoft Exchange Server have made us aware of the impact that security vulnerabilities can have on digital infrastructure and data protection.
We, too, are seeing a steady increase in broad, non-targeted and targeted attacks on our customers' applications and systems.
The most common attacks include:
As an engineering company for digital solutions and processes, the security of applications and infrastructure has been a central topic for many years and is always the focus of our projects. Since we usually have full access to the customer systems we manage, IT security and the data protection often associated with it is a cornerstone of everything we do.
GREEN-M INTERFACE DESIGN GmbH has implemented the following measures internally based on the BSI basic protection compendium and the Tisax certification of the German automotive industry:
Before we release an application into the "wild", we check the consistency and security of our source code with a security source code analysis and test the application for vulnerabilities with vulnerability scanners. With external penetration testing and the simultaneous elimination of the vulnerabilities found, we increase the security, data protection and availability of your applications.
From our experience in penetration testing, we have developed application hardening measures and ready-made plugins that can also protect systems such as Zend2, Shopware and WordPress against targeted attacks.
For WordPress we have developed the security plugin GREEN-M X-SECURITY 2.0, which has been confirmed in its security by multiple external penetration testing. For more information please contact us.
Programming errors responsible for security vulnerabilities often occur in applications at typical, systematically identifiable points in the code and configuration.
Static Code Analysis is performed semi-automatically and the findings of the tools used are evaluated, prioritized and eliminated in the development team.
We check the source code we create and third-party code within our development process with a security source code analysis and fix errors in the application. We document and monitor open source components for known security problems.

Most attacks are automated and usually pass quickly if the best-known vulnerabilities of an application have been fixed in time by updates and patches. If you want to test the security of an application in more depth and also prevent attacks from your own ranks, professional, manual penetration testing, also called pentesting, should take place. In a pentest, an attack on one's own system is simulated. The pentester uses the same tools and procedures as a real hacker.
Together with our partner Securai GmbH from Ingolstadt, we offer professional penetration testing and simultaneously eliminate the vulnerabilities found. Detailed reporting on the vulnerabilities helps to implement your compliance requirements in the area of application security.

As soon as security vulnerabilities of software solutions become publicly known, attacks on the corresponding gaps in the network have usually already begun.
Proactive monitoring of security vulnerabilities, their evaluation and defined processes help us to provide applications with the necessary updates and patches in a timely manner.
If a successful hack does occur, a backup concept helps to roll out a clean version of the application before the exploit.
Testing processes and the documentation of updates help in case of occurring errors that can be caused by the updates and patches.
At GREEN-M INTERFACE DESIGN, we generally perform updates and patches for every customer whose application we permanently support.
Applications usually offer their users the possibility to upload images and documents and thus also publish malware or links to compromised websites or forward them to other users or systems.
Conventional antivirus software installed on the web server often reaches its limits. GREEN-M relies on Sophos Intelix to have an engine with machine learning, deep learning, threat response, sandboxing and reputation control check all data inputs before they are stored in the application and block them in case of doubt.
Applications here can benefit from dynamic protection from one of the best endpoint protection providers in the world.
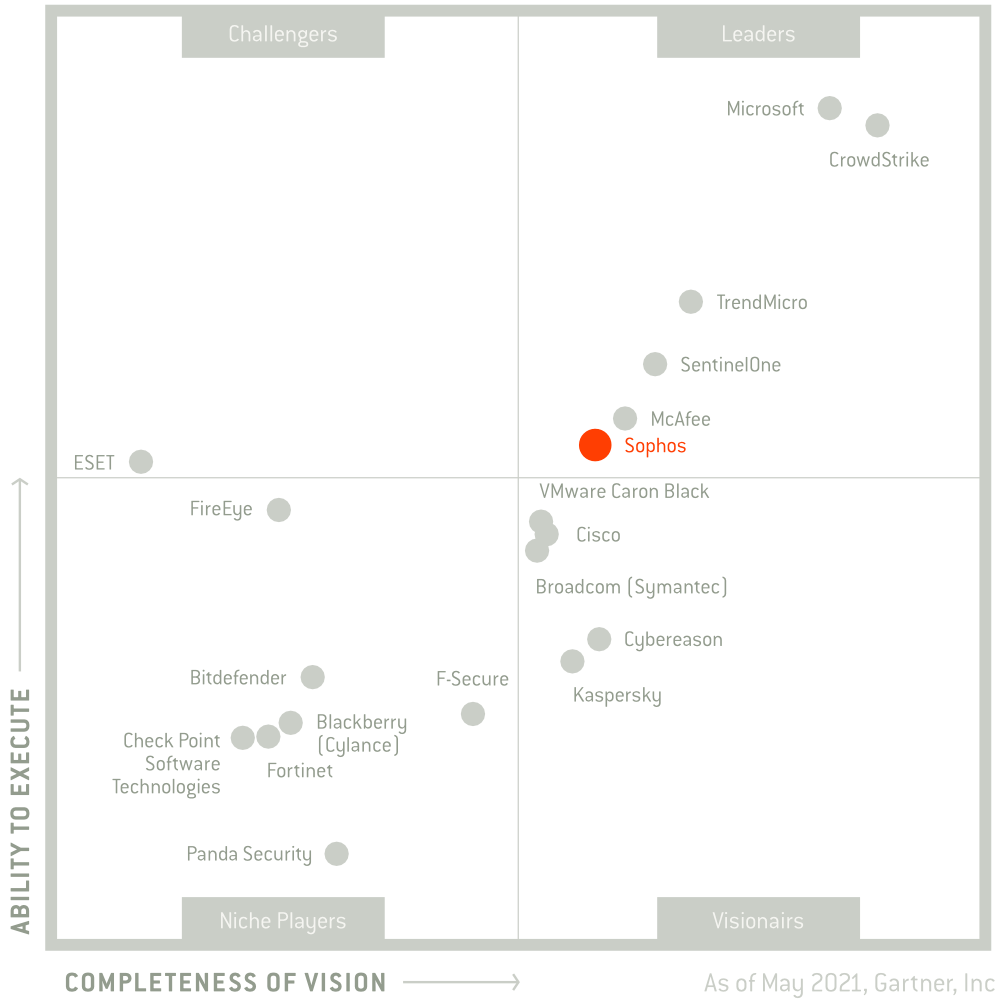
We handle the connection to the Sophos Intelix SaaS service on AWS and provide reporting or integration in a Security Information and Event Management.
Source Graphic: Gartner Magic Quadrant Endpoint Protection 2021

Vulnerability testing is a one-time or regular process to identify and classify security vulnerabilities in an application or network.
Regular scans reveal known vulnerabilities in applications, services, and networks, enabling their targeted remediation and strengthening of the system.
GREEN-M uses one of the leading scanners and thus detects the latest known vulnerabilities that can be exploited by hackers. We usually perform the scans quarterly or after updates and releases and evaluate the results together with our clients.
The security of an application also fundamentally depends on the security of the infrastructure in which it is embedded. Hosting, backups, access control and protection layers are the pillars of our infrastructure security and a key part of a security concept that views the protection of applications as a holistic concept. We work together with certified and proven service providers.
As a "Business Partner", we have been hosting our customers' applications uniformly on managed flex servers from Profihost GmbH in Hanover for almost 10 years. In addition to the flexible scaling of performance, we benefit from personal contact and extremely fast response times far from any hotline queue.
The systems are continuously provided with updates, patches and optimizations by Profihost and use the Gaia OS platform of the Israeli security company Checkpoint.
With the location in Germany, data protection can be implemented in accordance with German and European data protection laws.
For our customers with a Managed FlexServer Hosting at Profihost, we completely take over the communication with the hoster regarding scaling, performance, security and technical issues.




Identity and Access Management (IAM) is a framework of policies, processes, and technologies that enables organizations to manage digital identities and control and regulate user access to critical corporate data and applications.
By assigning users specific roles and ensuring they have the right level of access to corporate resources and applications, IAM improves security and the user experience, enables better business outcomes, and increases the feasibility of mobile and remote work.
Without identity and access management, it is almost impossible to track which user needs which rights for what and when, and how they use the access rights on a device in the first place. With IAM, you are guided confidently through this labyrinth of data.
We connect applications to existing IAM via SAML 2.0 or OpenID or provide the RED HAT supported open source solution "Keycloak" and support you with your company's identity management.



In distributed denial of service (DDoS) attacks, attackers use a large number of targeted requests to a web server in an attempt to overload the running services and crash the server and the applications hosted there. In most cases, bot networks of already hijacked computers are used for this purpose in order to launch a critical mass of requests. DDoS attacks are often part of an extortion campaign associated with money demands.
According to a survey, global attacks have increased by more than 500% in Q4 2021. In addition, the bandwidth of the BOT networks used is also steadily increasing.
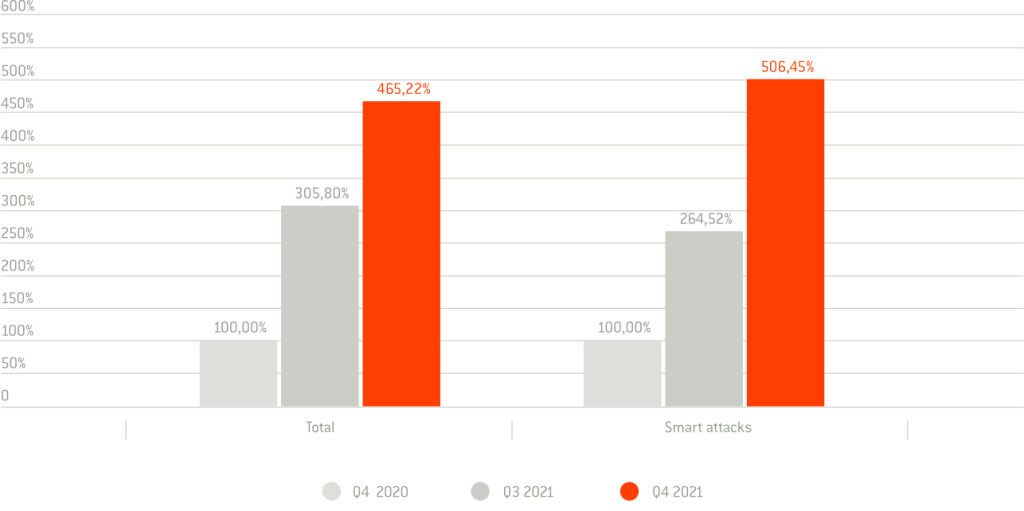
GREEN-M relies on the US-based provider Cloudflare, recommended by the German Federal Office for Information Security, to protect web servers. In addition to DDoS protection, the protection and performance of a website can be noticeably increased by a web application firewall (WAF) and a content delivery network (CDN).
Sources: https://securelist.com/ddos-attacks-in-q4-2021/105784/

A Web Application Firewall (WAF) is placed upstream of the web application and examines the incoming requests and the responses of the web server. The WAF thus provides protection against the most common attack scenarios, such as SQL injections, cross site scripting and zero-day exploits, and can also protect known and unknown vulnerabilities of a web application.
GREEN-M relies here on Cloudflare's global cloud solution and its centralized and active approach to firewall policy management:
GREEN-M takes care of the setup, configuration and monitoring of the web application firewall for you.
